What Is the CIA Triad and Why It Matter in Cybersecurity
Published: 3 Dec 2025
The CIA triad is one of the most important ideas in cybersecurity. It helps you understand how to keep information safe, accurate, and available when people need it. Many beginners hear the term and think it sounds complex, but it is actually simple once you break it down.
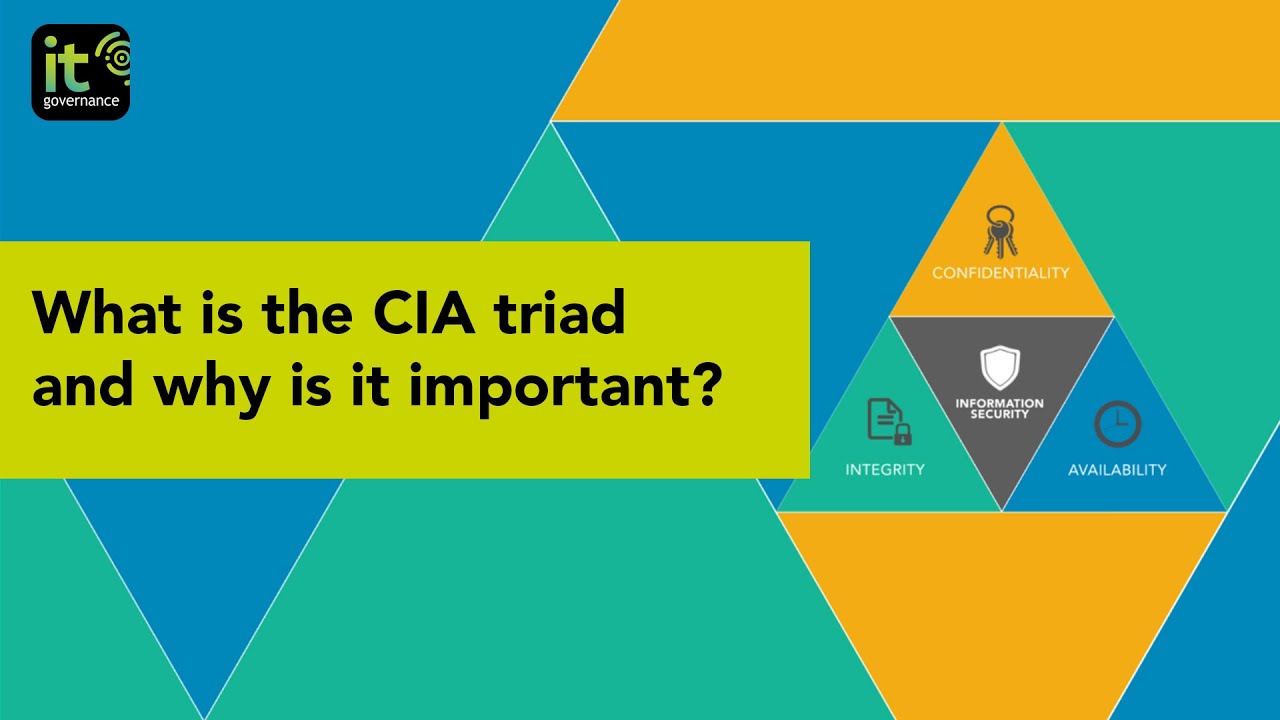
The CIA triad stands for confidentiality, integrity, and availability. These three parts guide almost every security decision in information security and network protection. You see it in businesses, schools, banks, and almost any place that stores digital information.
Think about a hospital. Doctors need access to patient data at all times. That is availability. The information must be correct, so no one gets the wrong treatment. That is integrity. Only the right people should see the patient’s records. That is confidentiality. The CIA triad supports all of this in the background.
Cybersecurity teams use the CIA triad to protect systems from attacks and accidents. It gives them a simple way to check if information is safe. You can use it too, even if you are new to the topic.
As you read this guide, you will learn how each part works, why it matters, and how it connects to real situations. You will also see examples that make everything easy to understand. This is the first step toward understanding how cybersecurity works.
What part of the CIA triad are you most curious about right now?
Table of Contents
Understanding Each Part of the CIA Triad
The CIA triad has three parts called confidentiality, integrity, and availability. Each part plays a different role, and together they create a strong security foundation. When you understand these parts, you can see how information stays safe in real situations.
Confidentiality
Confidentiality keeps information private. Only the right people can see it. Think about your online banking account. You enter a password because the bank needs to confirm your identity. This protects your personal details from unwanted access. Cybersecurity teams use tools like encryption, login controls, and secure passwords to maintain confidentiality.
Integrity
Integrity protects the accuracy of information. It makes sure data is correct and has not been changed without permission. Imagine a student’s grade report. If someone could change the numbers without being noticed, the system would lose trust. Integrity tools like digital signatures and audit logs help keep information clean and trustworthy.
Availability
Availability makes sure information is ready when someone needs it. You expect your favorite apps to load without delay. You expect hospital systems to work during emergencies. If a system goes down, it affects everyone. Cybersecurity teams use backups, extra servers, and monitoring tools to keep systems running.
These three parts work together like a team. They keep information private, correct, and accessible. When even one part fails, the whole system becomes weaker. Which part do you feel is the most important for your own digital safety?
What Is the CIA Triad in Information Security

The CIA triad plays a major role in information security. It helps organizations protect data in computers, servers, and cloud platforms. Information security teams use the triad to check if data is safe, correct, and ready for use.
Information security deals with everything that stores or handles information. This includes files, databases, websites, and devices. The CIA triad gives these teams a clear path to follow. They look at confidentiality to keep information private. They check integrity to make sure nothing has been changed. They watch availability to keep systems running.
Think about a company that stores customer details. They need strong passwords and access rules to protect confidentiality. They need monitoring tools to protect integrity so no one can change customer records. They need backups and a good server setup to protect availability so customers can access their accounts anytime.
Many security standards use the CIA triad as their base. This includes frameworks like NIST and ISO. These standards help companies stay safe and meet legal requirements. The triad gives them a simple way to build strong protection around their information.
You can think of the CIA triad as the heart of information security. It keeps everything working together in a clear and organized way. Want to move on to how the CIA triad works in network security?
CIA Triad in Network Security
The CIA triad also plays a key role in network security. Network security focuses on protecting the devices, systems, and connections that move information from one place to another. The triad helps teams keep these networks safe, stable, and trustworthy.
Confidentiality protects the information that travels through a network. For example, when you shop online, your payment details move across the internet. Encryption keeps those details private. It turns the data into a form that only the right people can read.
Integrity protects the accuracy of the information inside the network. Imagine a message being sent from one computer to another. Integrity checks make sure the message reaches the other side without any changes. Tools like hashing and secure communication methods help keep this data clean and safe.
Availability keeps the network running when people need it. Think about how frustrating it is when the internet goes down. In a business, this can stop work completely. Teams use backups, firewalls, and monitoring tools to keep networks active and stable. This helps prevent slowdowns and attacks that try to overload a system.
The CIA triad gives network security a strong foundation. It guides every step from protecting data on the move to keeping systems online. When all three parts work together, networks stay safe and reliable.
Purpose of the CIA triad in cybersecurity?
The CIA triad plays an important role in information security. Information security focuses on protecting data in computers, servers, cloud platforms, and storage systems. The triad gives teams a simple way to check if information is safe.
Confidentiality keeps private data hidden from the wrong people. Integrity keeps information correct and trustworthy. Availability makes sure the data is ready for use. These three ideas work together in every part of information security.
Imagine a company that stores customer information. The team uses strong passwords and access rules to protect confidentiality. They use monitoring tools to protect integrity and prevent unwanted changes. They use backups to protect availability so customers can check their accounts any time. All of these actions follow the triad.
The CIA triad also supports security standards like NIST and ISO. These standards help companies stay safe and meet legal rules. The triad keeps everything clear and organized so teams can make smart decisions.
Why the CIA Triad Is Important
The CIA triad is important because it helps protect information in every part of the digital world. It gives teams a simple way to understand what needs protection and how to manage risks. Without the triad, security work would feel confusing and unorganized.
Confidentiality protects private details and keeps unwanted users out. Integrity protects the accuracy of information so people can trust the data they read. Availability protects access to systems so work does not stop. These three parts support everything from small school systems to large company networks.
Think about a bank. Customers check their balances every day. They need private access. They need correct information. They need the system to work at all times. The triad supports all three needs. This is why it is the foundation of modern cybersecurity.
The triad also helps prevent attacks and failures. It guides teams as they build strong security systems. When a company follows the triad, it can avoid many problems and respond faster when something goes wrong.
Real World Examples of the CIA Triad
The CIA triad becomes easier to understand when you see it in real situations. These examples show how confidentiality, integrity, and availability work in everyday life.
Confidentiality Examples
Confidentiality protects private information from the wrong people.
Think about a doctor’s office. Patient records stay hidden from anyone who is not part of the medical team. The system uses secure logins to check who is trying to enter the files. This protects sensitive details.
Another example is online banking. Your account information is protected with encryption. This means the data is turned into a secret code that only the bank can read.
Integrity Examples
Integrity protects the accuracy of information.
Think about an online store. When you place an order, the system must keep the correct product, price, and address. Integrity tools check if the information stays the same during the process.
Another example is a grade report for students. If someone tries to change a grade without permission, the system records this action. This helps teachers trust the information.
Availability Examples
Availability keeps systems and information ready at all times.
Think about a streaming service. People expect it to work when they want to watch a movie. The service uses backup servers to stay online even when one server has a problem.
Another example is a hospital system. Doctors need quick access to patient information during emergencies. The system uses constant monitoring to stay active and stable.
These examples show how the CIA triad supports safety, accuracy, and access in real life.
Common Threats That Impact the CIA Triad
Many threats can weaken confidentiality, integrity, or availability. These threats can come from mistakes, accidents, or attackers. Understanding them helps you protect information more effectively.
Confidentiality faces threats like stolen passwords or unauthorized access. Imagine someone guessing a weak password and logging into an account they should not see. This breaks privacy and exposes personal information.
Integrity faces threats like data tampering. Attackers sometimes change information without being noticed. For example, a hacker might alter financial records or change product prices in an online store. This makes the data unreliable.
Availability faces threats like system failures and attacks that overload networks. A simple power outage can bring a system down. A cyber attack like a heavy traffic flood can stop a website from working. These problems keep users from accessing the information they need.
These threats show why the CIA triad is so important. It helps teams prepare for risks and keep information safe, accurate, and ready to use.
How to Apply the CIA Triad in Your Organization
You can use the CIA triad to create a stronger security plan for your organization. The triad gives you a simple way to protect information and reduce risks. You can follow a few steps to apply each part.
Start with confidentiality. Limit access to sensitive information. Give people access only when they need it to do their job. Use strong passwords, secure logins, and encryption to protect private files. For example, a school can protect student records by allowing only teachers and staff members to open them.
Next focus on integrity. Make sure your information stays correct and trustworthy. Use tools that track changes. Keep backups of important files. Set up alerts that notify you when someone tries to change information without permission. A company can use digital signatures to confirm that a document has not been edited.
Finally protect availability. Keep your systems running smoothly. Use regular backups, reliable servers, and monitoring tools. Create a simple plan for emergencies. For example, a hospital can use backup power and extra servers to stay active during a system failure.
These steps help your organization build a safe and dependable environment. The CIA triad keeps everything organized and easy to follow.
Conclusion
The CIA triad gives you a clear way to understand how information stays safe in the digital world. It explains why confidentiality, integrity, and availability matter in cybersecurity, information security, and network security. These three parts work together to keep data private, correct, and ready when people need it.
You can see the CIA triad in many real situations. A bank protects customer accounts from unwanted access. A hospital keeps patient records accurate. A school keeps its systems available for students. These examples show how the triad supports safety in everyday life.
The idea behind the CIA triad is simple. Protect privacy. Keep information correct. Keep systems running. When these parts are in place, people can trust the information they use. This builds confidence and creates a safer digital environment for everyone.
If you want to strengthen your own security, start by looking at these three areas. Ask yourself if your information is private. Ask if your data stays accurate. Ask if your systems stay available. These questions help you apply the CIA triad in a simple and effective way.
Understanding the CIA triad is a great step toward understanding cybersecurity. It helps you see how digital safety works and why it matters. Now you can look at your own systems with more confidence and make better choices to protect your information.
FAQs
What is the CIA triad in simple words
The CIA triad is a simple security model that explains how to protect information. CIA stands for confidentiality, integrity, and availability. Confidentiality keeps information private. Integrity keeps information correct. Availability keeps information ready when people need it. These three parts work together to keep data safe and trustworthy.
What is the CIA triad in cybersecurity?
The CIA triad is a core security model used in cyber security. CIA stands for confidentiality, integrity, and availability. Confidentiality protects private data from the wrong people. Integrity keeps data accurate and unchanged. Availability makes sure systems and information stay ready when users need them. The CIA triad helps teams build strong and reliable security for any digital system.
What is the CIA triad used for?
The CIA triad is used to guide how organizations protect their information and systems. It helps teams focus on confidentiality, integrity, and availability. Confidentiality keeps data private. Integrity keeps data accurate. Availability keeps data ready for users. The CIA triad is used to create security policies, build safer systems, and reduce risks in cyber security.

- Be Respectful
- Stay Relevant
- Stay Positive
- True Feedback
- Encourage Discussion
- Avoid Spamming
- No Fake News
- Don't Copy-Paste
- No Personal Attacks

- Be Respectful
- Stay Relevant
- Stay Positive
- True Feedback
- Encourage Discussion
- Avoid Spamming
- No Fake News
- Don't Copy-Paste
- No Personal Attacks