What Is Cybersecurity Architecture? A Complete Guide
Published: 31 Jan 2026
Cybersecurity architecture is a comprehensive framework that organizations design and implement to protect their IT infrastructure, digital assets, and sensitive information from cybersecurity threats. It functions as a blueprint for implementing security controls, policies, and protocols that safeguard critical digital assets. A well-structured cybersecurity architecture ensures data integrity, confidentiality, and availability. It proactively defends against escalating cyber threats, helping organizations identify and mitigate potential risks before they manifest.
The main benefits of cybersecurity architecture include proactive defense against disruptions, reduced downtime and financial losses, and disaster recovery integration. It also protects critical assets by safeguarding intellectual property and ensuring regulatory compliance and data protection. Furthermore, it preserves stakeholder trust through transparent communication during incidents and effective reputation management.
Cybersecurity architecture is mainly used to protect IT infrastructure, digital assets, and sensitive information. It is also used for maintaining business continuity, protecting critical assets, preserving stakeholder trust, and complying with standards and frameworks like NIST and ISO/IEC 27001.
The main parts or components of cybersecurity architecture include security policies and standards, Identity and Access Management (IAM), network security, endpoint security, data protection, Security Operations Center (SOC), and incident response and recovery. It also involves firewalls, intrusion detection/prevention systems (IDS/IPS), antivirus and antimalware software, and virtual private networks (VPNs).
Table of Contents
Cybersecurity architecture vs. traditional cybersecurity approach
Cybersecurity architecture differs from the traditional cybersecurity approach in several key aspects. Traditional cybersecurity measures are often focused on specific tools or reactive measures, while cybersecurity architecture takes a holistic and strategic approach beyond individual components. The emphasis in traditional cybersecurity is reactive, responding to incidents after they occur, whereas cybersecurity architecture is proactive, emphasizing strategic planning, continuous monitoring, and threat anticipation. Traditional approaches rely on isolated tools like antivirus and firewalls, while cybersecurity architecture involves planning, integration, and management of various security elements for a cohesive defense strategy.
Why is cybersecurity architecture important?
Cybersecurity architecture is critically important in today’s digital environment due to the ever-growing sophistication and diversity of cyber threats. It serves as the bedrock for safeguarding sensitive information, crucial business operations, and the overall integrity of digital ecosystems. A well-designed cybersecurity architecture is essential for maintaining business continuity, protecting critical assets, and preserving stakeholder trust. It aligns security measures with the overarching goals of the organization, thereby becoming an integral component of effective risk management.
Cybersecurity dynamics: Mesh, reference, diagram insights
The evolving landscape of cybersecurity is witnessing the emergence of innovative frameworks, with cybersecurity mesh architecture and cybersecurity reference architecture playing pivotal roles. Cybersecurity mesh architecture represents a dynamic approach that extends security controls beyond traditional perimeters, allowing for a more flexible and distributed defense strategy. It emphasizes the protection of individuals and devices regardless of their location, reflecting the modern reality of decentralized work environments. Complementing this, a cybersecurity reference architecture provides a standardized and comprehensive blueprint for designing robust security measures. It serves as a guide for organizations to structure their security frameworks, aligning them with industry best practices and regulatory standards. Visualizing the intricacies of these architectures is made tangible through a cybersecurity architecture diagram, a graphical representation that maps out the various components, connections, and interactions within a cybersecurity framework.
Key Components of Cybersecurity Architecture
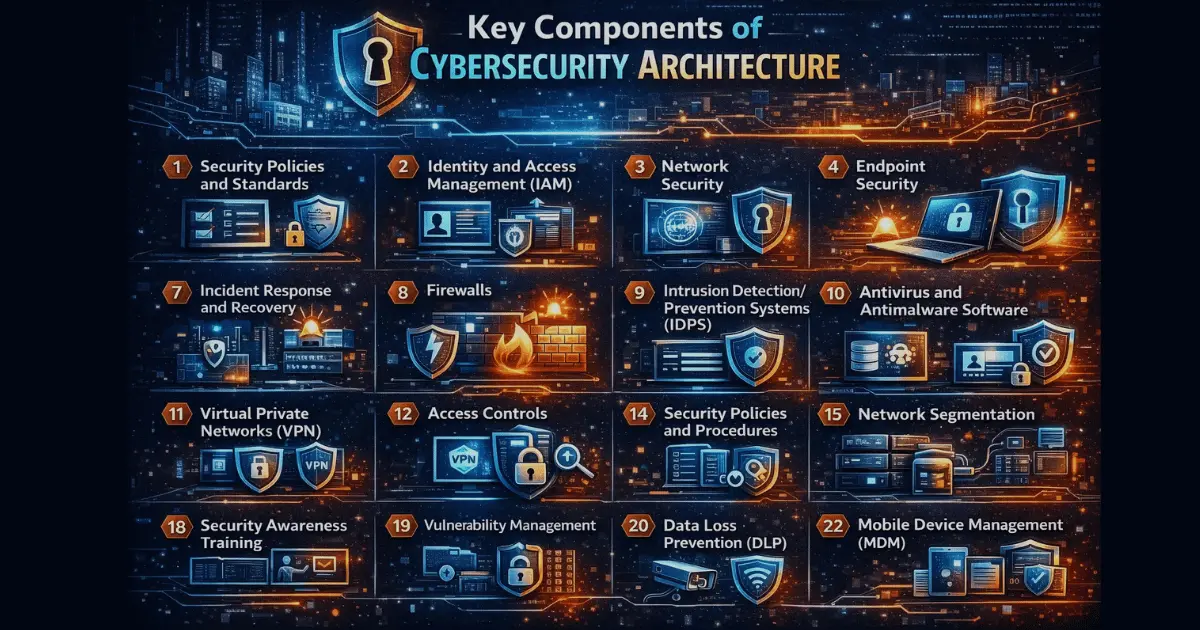
To build a truly resilient cybersecurity architecture, organizations must incorporate several essential components that address security at all stages – from initial threat detection to response and recovery.
Security Policies and Standards
A strong cybersecurity architecture starts with well-defined security policies and standards that establish the ground rules for system access, data handling, and information sharing. These policies should align with industry standards (e.g., nist cybersecurity framework, ISO/IEC 27001) and cover areas like password management, data classification, and incident response protocols.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is fundamental to secure access, ensuring only authorized individuals can access sensitive systems. It includes multi-factor authentication (MFA), single sign-on (SSO), and privileged access management (PAM), which help enforce the principle of least privilege. Modern IAM solutions may also leverage behavioral analytics to detect anomalies in user behavior.
Network Security
network security aims to protect the organization’s network infrastructure from unauthorized access, misuse, and attacks. This includes firewall configurations, intrusion detection/prevention systems (IDS/IPS), and network segmentation to isolate critical assets from the rest of the network.
Endpoint Security
With the rise of remote work, endpoint security has become increasingly crucial. It involves protecting laptops, smartphones, and iot devices that connect to the organization’s network from malware and other cybersecurity threats. Advanced endpoint security solutions offer features like automated threat detection, endpoint detection and response (EDR), and mobile device management (MDM) to enforce security policies.
Data Protection
Data is at the heart of every organization, and protecting it is paramount. This includes both at-rest and in-transit data encryption, data loss prevention (DLP) strategies, and data integrity monitoring. For instance, data encryption ensures that even if data is intercepted, it remains unreadable without the correct decryption key.
Security Operations Center (SOC)
The Security Operations Center (SOC) is a centralized function where a team of cybersecurity experts continuously monitors, detects, and responds to security incidents. SOCs are equipped with tools like security information and event management (SIEM) for real-time analysis and forensic investigations.
Incident Response and Recovery
Incident response and recovery focuses on minimizing the impact of security incidents. It includes incident detection protocols, predefined response playbooks, disaster recovery (DR) plans, and a business continuity plan (BCP). Effective incident response services and recovery capabilities enable organizations to return to normal operations quickly while limiting the damage caused by attacks.
Firewalls
Firewalls act as the first line of defense, monitoring and controlling incoming and outgoing network traffic. In cybersecurity architecture design, firewalls are strategically placed to filter and block unauthorized access, preventing malicious entities from compromising the integrity of the network.
Intrusion Detection/Prevention Systems (IDPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play a crucial role in identifying and responding to potential cybersecurity threats. IDS monitors network or system activities for malicious actions or security policy violations, while IPS actively prevents or blocks such activities.
Antivirus and Antimalware Software
Antivirus and antimalware software programs are designed to detect, prevent, and remove malicious software, including viruses, worms, and other types of malware.
Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) securely connect remote users or networks to the organization’s internal network over the internet, ensuring encrypted communication.
Access controls
Access controls are the gatekeepers of digital systems, determining who can enter, access, or modify specific resources. In the context of cybersecurity architecture, effective access controls are essential for maintaining the integrity of a system.
Encryption
Encryption ensures the confidentiality of data by making it indecipherable to unauthorized entities. Even if an intruder gains access to encrypted data, they will be unable to comprehend its meaning without the proper decryption key.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems collect, analyze, and correlate log and event data from various sources across an organization’s IT infrastructure to identify and respond to security incidents.
Security Policies and Procedures
Security policies and procedures are documented guidelines and rules that define the organization’s approach to cybersecurity, including acceptable use policies, incident response plans, and data protection policies.
Network segmentation
Network segmentation involves dividing a network into smaller segments to limit the impact of a security breach and prevent lateral movement of attackers.
Security Awareness Training
Security awareness training is a crucial component of cybersecurity aimed at educating employees and users about best practices in cybersecurity, potential risks, and the importance of adhering to established security policies.
Patch management
Patch management is a systematic approach to maintaining the security of an organization’s software, operating systems, and applications. The primary goal is to ensure that all systems are regularly updated with the latest security patches to address known vulnerabilities.
Vulnerability management
Vulnerability management is a proactive strategy focused on identifying, assessing, and prioritizing vulnerabilities in an organization’s systems and networks.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) encompasses technologies and strategies designed to prevent unauthorized access, use, and sharing of sensitive data within an organization.
Physical security measures
Physical security measures are implemented to protect the physical access to critical infrastructure components, such as data centers and server rooms, safeguarding against unauthorized entry and potential security breaches.
Wireless security
Wireless security is dedicated to implementing measures that secure wireless networks, including encryption, access controls, and monitoring.
Mobile Device Management (MDM)
Mobile Device Management (MDM) focuses on ensuring the security of mobile devices, including smartphones and tablets, used within the organization.
Compliance with standards and frameworks
Compliance with industry-specific regulations, standards, and cybersecurity frameworks is a foundational aspect of maintaining a baseline level of security and regulatory adherence. Examples include ISO 27001 for information security management systems and the nist cybersecurity framework for overall cybersecurity improvement.
Layers of Cybersecurity Architecture
Organizations should adopt a multi-layered cybersecurity architecture to defend effectively against cyber threats. This approach adds redundancy, addressing threats at multiple points, from the physical environment to application data.
Physical Layer
Physical security is often the first line of defense, protecting the hardware and infrastructure that store and process data. This layer includes security measures like biometric access controls, surveillance cameras, and physical access restrictions.
Network Layer
The network layer protects data flow between internal and external systems. It includes firewalls, IDS/IPS, and network segmentation. For example, network segmentation limits access between critical systems and other parts of the network, making it harder for attackers to spread malware across the organization.
Perimeter Security
This layer separates the organization’s internal network from untrusted external networks like the Internet. Components such as web application firewalls (WAFs), VPNs, and secure access service edge (SASE) solutions safeguard the perimeter.
Endpoint Security
As endpoints are a common entry point for attacks, securing them is essential. This layer includes antivirus solutions, EDR, and MDM, which help monitor and secure all endpoint devices.
Application Security
Application security involves practices and tools to secure software applications, such as static and dynamic application security testing (SAST and DAST). Developers must follow secure coding practices, perform regular vulnerability scans, and implement patch management to protect applications from threats like SQL injection and cross-site scripting (XSS).
Data Security
This layer safeguards data, ensuring it remains confidential and intact. Encryption is a key data security practice, especially for sensitive information such as customer records or intellectual property. Regular data integrity checks, data masking, and secure storage practices also protect data from unauthorized access and tampering.
Designing a Robust Cybersecurity Architecture
Designing cybersecurity architecture requires a methodical approach that aligns security initiatives with organizational goals.
Risk Assessment and Management
Understanding the specific risks faced by the organization is crucial for effective architecture design. Risk assessments help identify and prioritize assets based on their value and vulnerability to threats.
Threat Modeling
Threat modeling helps security teams identify potential attackers, attack paths, and threat impacts. Organizations can therefore implement defenses specifically tailored to counter likely threats.
Secure Design Principles
Incorporating secure design principles from the outset creates a more resilient architecture. Principles like “least privilege” ensure that users only have the access necessary for their roles, reducing the risk of insider threats. Similarly, “fail-safe defaults” ensure that systems automatically deny access if security checks fail.
Integration with Business Goals
Cybersecurity should be seen as an enabler of business continuity, not a hindrance. When cybersecurity goals align with business objectives, security controls can enhance productivity and customer trust.
Common Cyber Security Architectures
Organizations can choose from several cybersecurity architectures to enhance their security posture.
Zero Trust Architecture
zero trust assumes that no one, whether inside or outside the network, is automatically trusted. It requires strict identity verification for every user and device attempting access. This approach effectively minimizes risks associated with lateral movement by attackers, which is especially valuable for organizations with a remote workforce.
Defense in Depth
Defense in depth involves multiple layers of security controls to protect assets. For instance, an organization might combine network segmentation with endpoint security, firewalls, and IDS to create a layered defense. This approach mitigates risk by ensuring that even if one layer is compromised, additional layers continue to provide protection.
Layered Security
Layered security resembles defense in depth but focuses on segmenting specific security measures for different areas of the infrastructure. For example, network firewalls protect the network layer, while data encryption secures sensitive data. Layered security ensures that each area has a targeted security measure, providing comprehensive protection.
Micro-Segmentation
This approach involves segmenting networks into smaller, isolated zones. Micro-segmentation limits attackers’ lateral movement, as each zone has its access controls. It’s particularly useful in environments with hybrid or multi-cloud deployments, where isolating workloads can enhance security.
Implementing Cyber Security Architecture
Building a robust cybersecurity architecture requires a structured, phased approach to ensure security measures are comprehensive, sustainable, and adaptable to evolving cybersecurity threats.
Assess the Current Security Landscape
Begin by cataloging assets, data, users, and devices. Evaluate existing policies and controls to pinpoint gaps and redundancies. Maintain detailed records to help team members understand security priorities. Collaborate with teams across the organization to gather a well-rounded perspective and build trust.
Develop a Threat Model
Create a threat model to identify vulnerabilities and likely attack vectors. Rate each threat by impact and likelihood, and assess mitigations to prioritize high-risk areas. Use a simple high/medium/low scale to assess threats and initiate focused discussions on key risks. Keep the model up to date to adapt to new threats and organizational changes.
Document and Prioritize Improvements
After threat modeling, list necessary improvements and assign priorities based on impact and resources required. Evaluate opportunities based on their value and effort, categorizing them into short-, medium-, and long-term initiatives. Engage key stakeholders in reviewing priorities to ensure alignment on security goals.
Implement Quick Wins
Focus on high-impact, low-effort improvements that showcase immediate benefits, such as enabling MFA or enhancing spam filters. Select tasks that visibly enhance security to build confidence in the program. Opt for changes that bolster security without creating user friction to foster long-term support.
Develop a Long-Term Cybersecurity Roadmap
With foundational measures in place, plan larger initiatives, such as implementing SIEM systems, formalizing incident response, or executing network segmentation. Present the roadmap to leadership. Detail the expected impact, timelines, and resources required for ongoing support. Break down major projects into phases to track progress and demonstrate ongoing results.
Strategic planning for effective defense
Strategic planning is essential for effective defense in cybersecurity architecture, involving a comprehensive assessment of organizational needs and risks, defining clear objectives and goals, and budgeting and resource allocation.
Assessing organizational needs and risks
Before implementing cybersecurity architecture, organizations must conduct a comprehensive assessment of their needs and risks. This involves understanding the unique aspects of their operations, the types of data they handle, and the potential cybersecurity threats they face.
Defining clear objectives and goals
Strategic planning necessitates the definition of clear cybersecurity objectives and goals. These objectives should align with the organization’s overall business strategy.
Budgeting and resource allocation
Implementing cybersecurity architecture requires financial investment and resource allocation. Organizations must allocate sufficient budget and resources to ensure the successful execution of their strategic plan.
Continuous monitoring and adaptation
Continuous monitoring and adaptation are vital for maintaining an effective cybersecurity architecture, involving real-time threat detection, incident response protocols, and regular security audits and assessments.
Real-time threat detection
Continuous monitoring involves the real-time observation of network and system activities to detect anomalies or potential cybersecurity threats.
Incident response protocols
Cybersecurity architecture incorporates incident response protocols that dictate the steps to be taken in the event of a security incident.
Regular security audits and assessments
To ensure the ongoing effectiveness of cybersecurity architecture, organizations conduct regular security audits and assessments.
Scalability for businesses
Scalability is a key consideration for businesses implementing cybersecurity architecture, involving tailoring solutions to organizational size, modular and flexible design, and considerations for resource-constrained environments.
Tailoring solutions to organizational size
One of the strengths of cybersecurity architecture lies in its scalability. Implementing a scalable architecture involves tailoring solutions to the specific size and needs of the organization.
Modular and flexible design
A scalable cybersecurity architecture is characterized by a modular and flexible design. This allows organizations to add or adjust security measures as their needs evolve.
Considerations for resource-constrained environments
Smaller organizations may operate with resource constraints, making it crucial to prioritize security measures based on risk.
Business resilience through cybersecurity architecture
In the intricate dance between technology and security, the role of cybersecurity architecture extends beyond protection; it becomes a catalyst for business resilience.
Maintaining business continuity
Maintaining business continuity is a critical aspect of cybersecurity architecture, involving proactive defense against disruptions, reducing downtime and financial losses, and disaster recovery integration.
Proactive defense against disruptions
Cybersecurity architecture, with its proactive approach, serves as a shield against disruptions that could otherwise cripple business operations.
Reducing downtime and financial losses
In the event of a cyberattack, swift response mechanisms embedded in cybersecurity architecture minimize downtime. The ability to recover quickly reduces financial losses associated with business interruptions.
Disaster recovery integration
Business continuity within the cybersecurity architecture extends to disaster recovery planning. By integrating robust disaster recovery protocols, organizations can swiftly recover data and systems.
Protecting critical assets
Protecting critical assets is a key function of cybersecurity architecture, involving safeguarding intellectual property and ensuring regulatory compliance and data protection.
Safeguarding intellectual property
For many organizations, intellectual property is a cornerstone of competitiveness. Cybersecurity architecture employs encryption, access controls, and other measures to safeguard intellectual property.
Regulatory compliance and data protection
Protecting critical assets also involves compliance with regulatory standards. Cybersecurity architecture aligns with data protection regulations, ensuring that organizations meet legal requirements for the secure handling of sensitive information.
Preserving stakeholder trust
Preserving stakeholder trust is an essential outcome of effective cybersecurity architecture, involving building and maintaining trust, transparent communication during incidents, and reputation management.
Building and maintaining trust
Stakeholder trust is a delicate yet invaluable asset. Cybersecurity architecture plays a pivotal role in building and maintaining trust by assuring stakeholders that their data and interactions with the organization are secure.
Transparent communication during incidents
In the unfortunate event of a security incident, transparent communication is key to preserving stakeholder trust.
Reputation management
Cybersecurity incidents can impact an organization’s reputation. Cybersecurity architecture includes measures for reputation management, helping organizations recover trust through transparent communication, swift resolution, and ongoing efforts to enhance security measures.
Challenges and Best Practices
While developing and maintaining a cybersecurity architecture, organizations face numerous challenges.
Address Security Gaps
Security gaps often emerge due to outdated technology, lack of visibility, or misconfigurations. Regular security assessments, vulnerability scans, and penetration testing can help uncover these gaps.
Balance Security and Usability
Overly complex security measures can hinder productivity. Aim for security solutions that integrate seamlessly with daily workflows, like SSO, for easy access without compromising security.
Keep up with Emerging Threats
The cyber threat landscape is constantly evolving. Stay updated by subscribing to threat intelligence feeds, joining industry groups, and attending security conferences.
Conduct Regular Audits and Compliance
Compliance is a baseline but essential to maintain trust and operational integrity. Conduct regular audits to ensure adherence to relevant regulations (e.g., GDPR, HIPAA) and internal security policies.
Train and Increase Employee Awareness
Human error remains a top vulnerability in cybersecurity. Offer ongoing training sessions to educate employees about phishing, social engineering, and safe data practices.
Common challenges in implementing cybersecurity architecture
Implementing cybersecurity architecture comes with its share of challenges. Understanding and addressing these hurdles are crucial for organizations striving to establish a resilient defense.
Lack of understanding and awareness
Organizations may lack a clear understanding of cybersecurity architecture, necessitating investment in cybersecurity education.
Resource constraints
Many organizations, especially smaller ones, struggle with budget constraints for cybersecurity initiatives.
Complexity of integration
Integrating cybersecurity with existing systems can be complex, requiring careful planning and testing.
Evolving threat landscape
Adapting to the rapidly changing threat landscape requires continuous monitoring and threat intelligence integration.
Regulatory compliance
Navigating complex regulatory requirements is time-consuming, requiring dedicated efforts.
Insider threats
Balancing trust and security is delicate, requiring the implementation of user behavior analytics and robust access controls.
Lack of standardization
Diverse security frameworks make standardization challenging, requiring organizations to navigate varying standards.
Factors to consider for the long-term effectiveness of cybersecurity architecture
As organizations invest in cybersecurity architecture, ensuring its long-term effectiveness is paramount.
Alignment with business objectives
Cybersecurity architecture should align with the overarching business objectives of the organization.
Comprehensive risk assessment
Periodic risk assessments help organizations identify new threats, vulnerabilities, and potential impacts.
Robust incident response planning
Developing incident response plans based on realistic scenarios enhances preparedness.
Integration of emerging technologies
Cybersecurity architecture should be adaptable to integrate emerging technologies.
Employee training and awareness
Regularly educating employees about cybersecurity best practices is essential.
Regulatory compliance
Ensuring ongoing compliance with industry-specific and regional regulations is vital.
Vendor management
Regularly evaluating and assessing the security practices of third-party vendors is crucial.
Data lifecycle management
Classifying and categorizing data based on sensitivity allows for targeted security measures.
Regular security audits
Conducting regular independent security audits provides an unbiased assessment of the effectiveness of cybersecurity measures.
Executive leadership involvement
Executive leadership should demonstrate a commitment to cybersecurity by actively participating in decision-making and resource allocation.
Final Thoughts
Building a robust cybersecurity architecture proves crucial for organizations aiming to protect sensitive data and assets within an increasingly hostile digital landscape. Implementing a structured approach—assessing the existing landscape, developing a threat model, prioritizing improvement opportunities, and focusing on quick wins – helps you create a security strategy that addresses current vulnerabilities while adapting to emerging cybersecurity threats.
Wrapping up
In today’s dynamic digital world, robust cybersecurity architecture is a strategic imperative, serving as a proactive defense against a range of cyber threats. It ensures business resilience, protects critical assets, and preserves stakeholder trust. Continuous improvement through regular assessments, incident response testing, training, and audits is crucial for a resilient cybersecurity posture that evolves with the changing threat landscape. As organizations navigate the digital frontier, cybersecurity architecture becomes a vital strategic compass in an era defined by technological dynamism.
FAQs
What is the purpose of developing a cybersecurity architecture?
The primary purpose of developing a cybersecurity architecture is to provide a comprehensive and layered approach to defending against cyber threats. Organizations can protect against unauthorized access, data breaches, and other security incidents by structuring security measures across various layers and components.
How does zero-trust architecture improve cybersecurity?
Zero-trust architecture enhances security by requiring strict identity verification for every user and device trying to access network resources. Additionally, this model minimizes the risk of unauthorized access and lateral movement within the network.

- Be Respectful
- Stay Relevant
- Stay Positive
- True Feedback
- Encourage Discussion
- Avoid Spamming
- No Fake News
- Don't Copy-Paste
- No Personal Attacks

- Be Respectful
- Stay Relevant
- Stay Positive
- True Feedback
- Encourage Discussion
- Avoid Spamming
- No Fake News
- Don't Copy-Paste
- No Personal Attacks






